Achieve SOC 2 Compliance and Security Posture Management Maturity with Minimal Spend
Achieve SOC 2 Compliance and Security Posture Management Maturity with Minimal Spend Leveraging Tauruseer's differentiated Cloud-Native Application Protection Platform (CNAPP): Security Posture Analytics + Cognition Engine (SPACE™), Purpose-Built for Growth SaaS Startups and Small to Midsize Businesses.

INTRO
If you're looking for a simple introduction to SOC 2 requirements, you won't find it here. But if you're serious about obtaining SOC 2 compliance and making audits easier, you're in the right place. As a modern security platform, we understand the challenges of implementing SOC 2 controls and the impact it can have on your organization's compliance and risk management.
We know that SOC 2 compliance is no longer just a "nice-to-have" but a must-have for organizations that want to stay competitive in today's market. Your customers, management team, partners, investors, and insurers are likely demanding it, and it's crucial to meet those demands. Our approach is not to just help you pass an audit, but to build a robust security program that protects your organization from cyber threats while achieving regulatory compliance — at a fraction of the costs of traditional approaches.
Our integrated approach combines the power of GRC mindset with the security and scalability of a CNAPP platform, helping you automate security processes, gain real-time insights into your security posture, and manage compliance requirements across your entire product portfolio and multiple cloud environments. This means you can implement SOC 2 controls efficiently and cost-effectively while reducing the risk of non-compliance penalties.
So, whether you're new to SOC 2 compliance or looking to enhance your existing program, we can help. Our experts are here to guide you through the process, so you can focus on your core business while we help you achieve your compliance goals.
.
Tauruseer SOC 2 Approach Intro
At Tauruseer, we believe that by combining the spirit of GRC means with Security Posture Management, organizations can achieve a unified approach to managing their security risks. Our SPACE™ Platform combines these ideas to provide organizations with a comprehensive and integrated solution to help them achieve their security and compliance objectives.
The Tauruseer SPACE™ Platform includes application security posture management (ASPM), software supply chain security (SSCS), and cloud security posture management (CSPM) capabilities, which are integrated into a single platform. This allows organizations to manage their security posture from code to infrastructure, ensuring their products are continuously secure and compliant by default.
By overlaying cognitive security analytics XDR, the SPACE™ Platform can help teams proactively prevent, detect, and respond to security threats in real-time, protecting their cloud product portfolio and data from external attacks and regulatory challenges. Tauruseer's approach goes beyond simply documenting compliance but integrates proactive and preventive security actions, improving the overall security posture of the organization.
By combining GRC concepts with Security Posture Management, organizations can achieve a more proactive, preventive, and protective approach to managing their security risks. Our platform provides a unified solution that allows organizations to achieve SOC 2 compliance and meet their regulatory requirements.
But First, Understand the Cybersecurity Paradigm Shift
The shift in cybersecurity's paradigm from a reactive to a proactive strategy (i.e., Security Posture Management) reflects a change in emphasis from simply responding to security incidents to proactively managing an organization's overall security posture.
This change acknowledges that security is about more than just warding off attacks; it also requires a constant state of readiness to deal with new and emerging threats. To better comprehend and manage risk, businesses can benefit from security posture management, which takes a holistic approach to security by taking into account people, processes, behaviors, and technology. Methods like implementing best practices, keeping up with software vulnerabilities, and frequently testing and reviewing systems and securing processes are all part of this strategy. Organizations can better manage risk, enhance their security posture, and lessen the effect of security incidents by adopting a more proactive, preventive, and protective stance.
Now, Understand the Governance, Risk & Compliance (GRC) Tools Paradigm Shift
Governance, Risk, and Compliance (GRC) tools are also in need of a change in due to the aforementioned shift in the cybersecurity paradigm. Tools for tracking and documenting an organization's adherence to applicable regulations and standards have historically concentrated on workflows and snapshots for evidence collection. This is no longer enough.
There has been a change, however, in thinking toward integrating security automation, integration, security analytics, and security actions into a next-gen GRC platform strategy in response to the growing sophistication of cyber threats and the necessity of more proactive risk management. Therefore, GRC tools must now offer a more all-encompassing solution, one that includes not only the documentation of compliance but also the automation and integration of security processes, as well as the distribution of security actions to the appropriate individuals in order to mitigate risks in real time.
The point is to give businesses a central hub from which they can demonstrate conformance while also keeping tabs on and controlling their security posture in real time. This requires a shift to measurable
(P)erformance-Oriented GRC, or GRC(P). Organizations can improve their security posture and obtain improved risk and compliance outcomes by incorporating security automation, integration, and actions into GRC(P). By automating and integrating security processes like vulnerability management, incident response and threat intelligence, businesses are better able to react to security events and contain their damage. Organizations can also improve their security posture and reduce their vulnerability to attacks by adopting proactive, preventive, and protective measures.
History on GRC Tools for SOC2 Compliance
- Legacy GRC tools: The majority of businesses with first-generation GRC systems are dissatisfied with them due to their complexity, inability to be upgraded easily, poor user interface, excruciatingly long to achieve ROIs, and lack of value delivered. Solution evaluations frequently reveal that isolated implementations were made rather than enterprise-wide rollouts. Also, the project either ceased or grew significantly more difficult after the initial use case was implemented. The promise to be transformative is lost and turns into a technological initiative taking business away from its core business. These are tools like RSA Archer, Service Now, IBM, etc.
- Newer GRC tools: These are tools like Vanta, Drata, Secureframe, etc. that make outlandish promises like, "SOC 2 compliant in two weeks." Don't be fooled, these solutions aren't really for you, they are for auditors. Meaning, the use case is to speed up an audit. There is much more to do to prepare for, and implement, to achieve SOC 2 compliance. These are technologies that need to be deployed and proven to used effectively. Also, make not mistake, these auditor tools are for demonstrating compliance, not to help with security (even though that's what they claim). They help release some productivity during time of the audit process so other work can be done for security purposes. But this is not security. It just makes the audit less disruptive for your IT teams during the time of the audit. The tools help you gather evidence, keep an eye on SOC 2 compliance, and give you transparency over your compliance status of particular regulatory requirements. This proof is saved in the auditor tool so that you don't have to send screenshots and spreadsheets to your auditor to show that you're following the rules. Most auditor tools have boilerplate policy documents that have been approved by auditors and can be used as a starting point. Most of these policies are not measurable, but hey, you keep track of them and retrain people on policies manually. Are they following them though, who knows? Ask yourself is this security, or do I have a false sense of security?
Everyone seems to be missing the point, which is that security is an ongoing activity that must be included into our regular routine. This is not a one-and-done deal before the frightening auditor checks everything. To stay aligned with compliance means security is getting done daily and is an integral component of achieving business growth objectives.
Pulling The Paradigm Shifts Together in a CNAPP: The Better Approach
Integrating GRC(P) concepts into a Cloud Native Application (CNAPP) platform can have a transformative impact on an organization's security posture. By bringing together the power of GRC tools and the scalability of Tauruseer's SPACE™ Platform, organizations can manage their security risks more effectively, improve their regulatory compliance, and enhance their overall security performance.
With GRC(P) embedded in the SPACE™ Platform, organizations can automate security processes such as vulnerability management, incident response, and compliance management, reducing the workload on security teams and minimizing the risk of human error. By leveraging the analytics and insights generated by the SPACE™ platform gain real-time insights to enable quick identification and resolution of security issues.
The integration of the SPACE™ Platform also ensures that security is an integral part of an organization's software development lifecycle and cloud operations processes. By embedding security controls in the SPACE™ Platform, security becomes a "built-in" feature of an organization's cloud-native applications, rather than an afterthought.
Moreover, by using a single platform, organizations can achieve a higher level of compliance and reduce the time it takes to achieve and maintain SOC 2 compliance. The SPACE™ Platform provides a centralized repository of compliance-related controls and auditable traceability, making it easy to manage and track compliance across the entire cloud product portfolio.
In conclusion, integrating the SPACE™ Platform can help your organization achieve better outcomes and reduce the risks of security breaches at the speed of innovation.
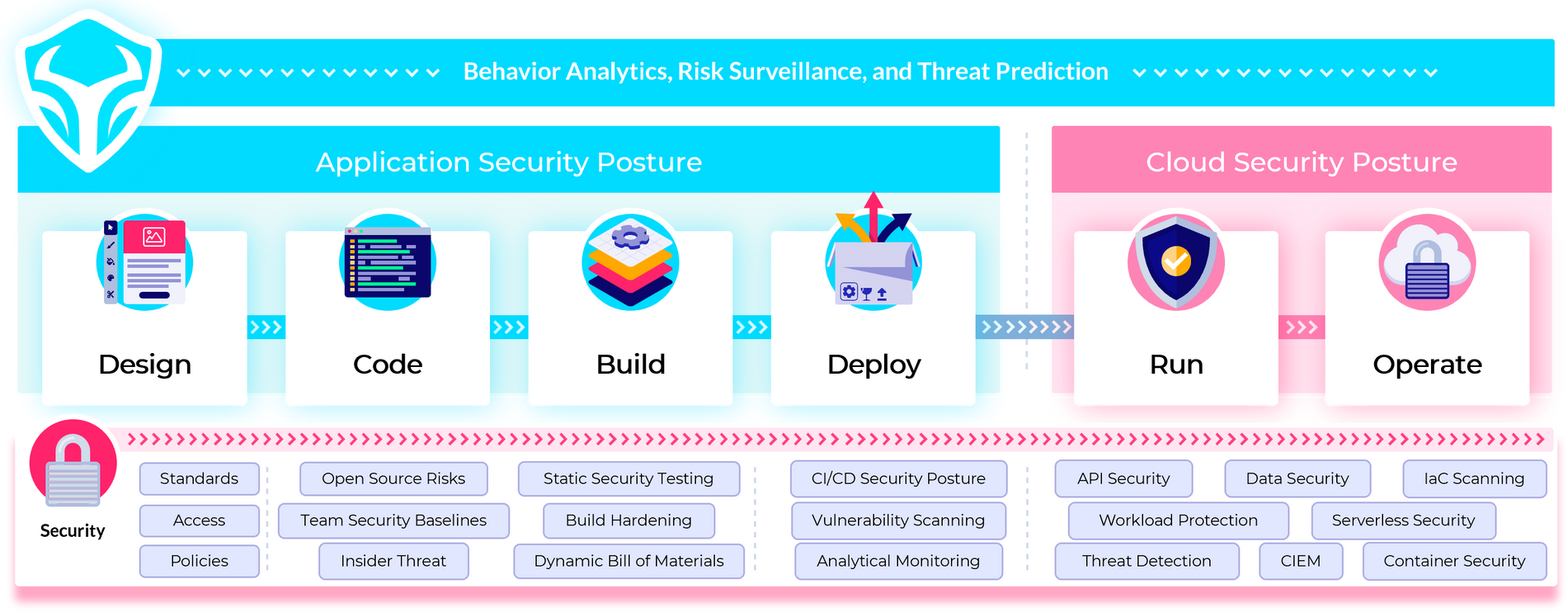
Roadmap to Security-First, Cost-Efficient SOC 2 Compliance
Because efficient use of resources is crucial, questions about price are generally the first to arise. Depending on the size and complexity of your firm, the cost of achieving SOC 2 compliance may range from moderate to high. Many businesses may spend more than $100,000 annually on SOC 2 Type 2 implementation and upkeep. This is in addition to the price tag attached to conducting the audit.
In order to get your security program and technology up and running, most businesses don't have an additional $100,000+ to spend on compliance. It makes no sense to put additional resources into compliance in order to give yourself a false sense of security rather than protecting the organization with real security. But, as you are likely experiencing, failing to attest to compliance can be a hindrance to expansion and winning new sales prospects.
To get around this catch-22, we have laid out a roadmap for how Taursueer can enhance your security posture management maturity while helping you achieve many of the SOC 2 compliance requirements at a fraction of the expense of the annual penetration test.
*NOTE: The following sections are best read on your desktop computer.
Secure Development | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Source Code Management (SCM), Developer & Product Team Correlation | Github, GitLab & Bitbucket + Tauruseer | $0.00 | There are three popular Git source code management solutions, and all of them provide a free basic plan. Tauruseer collects metadata about the code and correlates people, CI/CD pipeline tools, and cloud resources with each product team's code and their security vulnerabilities. |
| Code Review Automation & Correlation | Git PR + Tauruseer | $0.00 | Put your Git repos under the scrutiny of pull requests and dynamic analytical monitoring of each product team’s security protection baselines. Tauruseer is compatible with the three most popular Git SCM tools on the market today: Bitbucket, Github, and GitLab. This integration allows Tauruseer to provide analysis and compliance reporting to verify each product team’s: authors and timestamps, tools used and configurations when creating code (pedigree), source of code and third-party dependencies (provenance), and the integrity of the supply chain (authorized identities). Tauruseer then flags for potential malicious modifications. |
| Software Composition Analysis (SCA) Automation & Correlation | Tauruseer + Snyk or Dependabot | $0.00 | Tools for software composition analysis (SCA) reveal both the open-source software components you use and any security vulnerabilities in the third-party dependency code that your apps rely on. Tauruseer offers a free solution out-of-the-box that can be enhanced by Snyk’s commercial solution that has a free starter plan. If your project's code is hosted on Github, you can use the free service Dependabot as well. |
| Open Source License Risk & Correlation | FOSSA + Tauruseer | $0.00 | All open source dependencies utilized in your work, together with their respective licenses, must be tracked and managed. Your code could be at risk if you misuse the open source license. FOSSA is an app that checks for both security and compliance. Small groups can take use of no-cost license compliance services and have that information correlated to the specific product teams with the Tauruseer platform for continuous monitoring. |
| Static Application Security Testing (SAST) Automation & Correlation | SonarQube + Tauruseer | $0.00 | Static application security testing (SAST) tools looks at an application's code and analyzes it to find security flaws, including OWASP Top 10 without actually running the code. SonarQube is an SAST scanner that has a powerful free community edition and works with a variety of languages and frameworks. Integrates with major CI pipelines, IDEs, and works well with Docker Hub or Kubernetes. SonarQube can be self-managed or as-a-service. |
| Dynamic Application Security Testing (DAST) Automation & Correlation | OWASP ZAP | $0.00 | Automatic testing for a wide variety of real-world threats is possible using dynamic application security testing (DAST) solutions. Web application testing tools often examine the application's HTML and HTTP front ends. Use it to scan your applications for security flaws from the outside, simulating the kinds of attacks that hackers from outside your organization would try. It's easy to get started with the OWASP ZAP web scanner because it's open source and available for no cost. |
Extra Secure Development Capabilities | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Dynamic Software Bill of Materials (SBOM) | Tauruseer | $0.00 | Tauruseer's patented PIRATE™ Risk Model builds contextual (on every product team), dynamic Software Bill of Materials (SBOM) every time code changes, creating powerful software supply chain security and compliance. Gain a complete inventory and continuous awareness of code risks, even after deploying to the cloud.. |
| Pipeline Bill of Materials (PBOM) | Tauruseer | $0.00 | A software bill of materials (SBOM) is the code inventory that goes into making a software application. Including their vulnerabilities. Dynamic SBOMs help organizations or people avoid (or fix) using software that could hurt them. A pipeline bill of materials (PBOM) goes beyond that inventory of software code components and looks at the whole process, the tools used in each team’s CI/CD pipelines, their configurations, and tells you the risks from design to production, not just the code. Because it looks at all the ways an attack could happen, PBOMs are better at helping people avoid security issues and defects. |
| Team Security Baselines | Tauruseer | $0.00 | Employ automatic analytical monitoring where the PIRATE™ Risk Model learns each team's developers, tools used, controls configurations, source of code, and CI/CD integrity to flag risky changes of the trusted baseline for review and verification. |
| Build Process Hardening | Tauruseer | $0.00 | Further operationaling the Team Security Baselines and Dynamic SBOM capabilities via the PIRATE™ Risk Model, Tauruseer identifies potentially malicious code modifications and access to repos that may be insider threat. |
| CI/CD Security | Tauruseer | $0.00 | Adversaries target CI/CD tools, environments, and systems to spread malware, steal secrets, abuse code flaws, and more. With Tauruseer, continuously monitor for OWASP Top 10 CI/CD Security Risks and more. |
| Continuous Assurance | Tauruseer | $0.00 | Automate team-based analytical remediation verification: source code commits (Jenkins) to version control repository (GitHub) correlated to work item tracking (JIRA) with proprietary scanning to validate code fixes. |
| Zero-Day Code Vulnerabilities | Tauruseer | $0.00 | Using the SBOM that Tauruseer generates, you can query your entire product portfolio and instantly identify vulnerabilities like Log4J, see what products and their dependencies are affected, and prioritize fixes based on business importance. |
People Security | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Employee Onboarding & Offboarding | Tauruseer + HR Service Management or JIRA | $0.00 | Employ the onboarding/offboarding features of your HR Service Management system (e.g. Vensure, Rippling, or BambooHR) correlated with Tauruseer's product centric, role-based access monitoring. Alternatively, you may create a new HR project in your existing ticketing system (like JIRA) and assign a pre-made checklist to each issue. |
Extra People Security Capabilities | Total Extra Cost $12,500.00*
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Behavior & Insider Threat Analytics | Tauruseer | $0.00 | Behavior analytics detects and prevents insider threats by monitoring and analyzing the actions and routines of software developers. Checking for odd or suspicious activity that could suggest a security issue involves keeping an eye on things like code modifications, system access, and communication patterns. The purpose is to keep sensitive information safe from unauthorized access or theft and to stop malicious or inadvertent damage to software systems. |
| Integrated Secure Code Training | Secure Code Warrior or Immersive Labs | Starting at $12,500/year | Tauruseer is a integrated developer secure code training solution allows cloud-native companies to optimize processes that support product teams. Tauruseer gives you a full set of tools to find risks, gives continuous feedback to specific teams, and closes the loop between training and doing the work. It gives you the data and in-line insights you need to improve operational excellence day after day and year after year. |
| Developer Training & Performance Analytics | Tauruseer | $0.00 | Monitoring and analyzing developer actions to assess how well they handle threats and fix security flaws is what Tauruseer's activity analytics is all about. Metrics such as the number of risks found and remediated, the rate at which vulnerabilities are fixed, and the success of security education over time. To better address vulnerabilities, it is important to learn how well developers are handling security concerns and where they may make improvements. With this knowledge, businesses can better protect their software systems and sensitive data from potential threats. |
Governance | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Software Asset Discovery & Inventory | Tauruseer | $0.00 | Tauruseer comprehensive software asset discovery and inventory fetches data continuously from code repos and CI/CD tools to ensure unmanaged assets don't turn into forgotten shadow IT or abandoned code, creating more insecure attack surfaces. |
| Policies & Procedures | Tauruseer | $0.00 | Create measurable SDLC governance policies and rules for controls, code, cloud resources, dependencies, technologies, tools, services, and OSS licenses. Get instant adherence or alerting to noncompliance and track fixes. |
| Risk Assessment | Tauruseer | $0.00 | The first stage in any good security governance program is a thorough risk assessment. Regulations and compliance standards like HIPAA and GDPR make this a necessary action. A risk evaluation, while necessary annually, is a time-consuming endeavor that can consume several days or even weeks. Though there is no shortage of risk management software that seek to address this issue, each one represents yet another tool and expense. By combining Tauruseer with an issue tracking system like Jira, you can cut down the time it takes to complete this task from days to hours with no extra tool expenses. |
| Vendor Monitoring | Tauruseer | $0.00 | Inside-out SaaS vendor monitoring is a disruptive approach to security management that shifts the burden of monitoring security to the vendor. This approach involves the vendor proactively monitoring their own security posture to identify and address vulnerabilities before they can be exploited, which can lead to more effective and efficient security management. By taking this approach, vendors can ensure they are meeting their SLAs related to security and build trust with customers. A third-party vendor registry and read-only monitoring dashboards can be kept in Tauruseer. |
Extra Governance Capabilities | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Continuous Controls Monitoring (CCM) | Tauruseer | $0.00 | Set a controls maturity level on every product team to enforce the deployment of controls and automate Continuous Controls Monitoring (CCM) that detects effective configuration settings, configuration drift, removal of a control, and risk performance of every team. |
| Product Portfolio Management (PPM) | Tauruseer | $0.00 | Gain visibility of risk governance across the entire portfolio of software products to ensure success and stability. Automate analytical monitoring to illuminate worst and best performing teams & portfolios. |
| Stakeholder Dashboarding | Tauruseer | $0.00 | Automate progress tracking for specific customers, auditors, executives and managers of SecOps, DevOps, Engineering, and GRC to provide a overview of KPIs and relevant data to help make informed risk decisions. |
Change Management | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Ticketing & Approval | Tauruseer + JIRA | $0.00 | As a developer, you almost certainly already use JIRA (or a similar tool) to log and monitor work items. Production change tickets and their approval can be monitored in the same issue tracking system. Integrating Tauruseer into your CI/CD workflow with cognitive security analytics that enables change management tracking and code commit activity. |
| Deployment | Tauruseer + Jenkins, GitHub Actions, Travis CI | $0.00 | If you're looking for a free CI/CD option, Travis CI and Github Actions are your best bet. CircleCI and Jenkins are just two examples of the many options out there. |
Extra Change Management Capabilities | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Risky Changes | Tauruseer | $0.00 | Integrating Tauruseer as the security event and assurance correlation engine into your CI/CD workflow enables role-based analytical tracking of activities such as source code commits (Jenkins) to version control repository (GitHub, etc.) correlated to work item tickets (JIRA). Whenever there is a deviation from established procedures or the suspicion of an insider threat, the relevant managers and team dashboards are notified automatically so that the issue can be investigated. |
Vulnerability Management | Total Extra Cost $10,000.00*
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Vulnerability Scanning | Tauruseer + Azure Defender or AWS Inspector | $0.00 | AWS Inspector can be activated in your AWS environment if your cloud-native firm wants to perform vulnerability scans of your EC2 instances and applications . It's basic and free for the first 250 instance assessments, but it lacks features. Azure Defender for Cloud matches AWS Inspector. Its vulnerability scanning is better than AWS Inspector for this article. Like Amazon Inspector, it is easy to use and suits Azure businesses that favor Azure services. |
| Penetration Testing & Correlation | Tauruseer + Penetration Testing Service | Starting at $10,000 | At least once a year, it's recommended that you hire a security expert to conduct a full-fledged penetration test rather than relying on an automated tool. When it comes to creating secure products, time is of the essence, and the Tauruseer platform provides our partners with cutting-edge, context-aware pen-testing correlation to provide real-time insight into the attack surface of applications to eliminate real vulnerabilities more quickly. |
| Centralized Vulnerability Management | Tauruseer | $0.00 | Normalize the data, aggregate, and correlate the results of various vulnerability scanners and gain visibility into a single place for easy management. |
Extra Vulnerability Management Capabilities | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Intelligent Prioritization | Tauruseer | $0.00 | Prioritize the right actions to the right people. Tauruseer's Cognition Engine cuts through the noise to reveal hidden risks and high-impact opportunities with automated analytics, correlation, and pre-defined logic combined with machine learning methods to discover, examine, and prioritize intelligently. |
| Toxic Combinations | Tauruseer | $0.00 | From the perspective of cloud-native application security, Tauruseer illuminates toxic combinations, for example: the product is publicly accessible, it handles sensitive data that is subject to PCI DSS regulations, it has a large user base, the Product Team has low visibility into their process risks, there are a large number of vulnerabilities present...... |
| High-Impact Opportunities | Tauruseer | $0.00 | In vulnerability management, Tauruseer automatically prioritizes high-impact opportunities, for example, where a Common Vulnerabilities and Exposures (CVE) is a level 7 and is highly exploited, affects 100 products across the entire product portfolio is considered more crucial to fix than a CVE that is a level 10 and only affects 1 product. |
| Most Improved Product Team | Tauruseer | $0.00 | Tauruseer constantly tracks a variety of indicators on to highlight product teams that have successfully improved their risk management and where they still need to focus their efforts. They pertain to reducing risks over time through monitoring integrations, risk remediation performance, security hygiene, and team performance on each product team. |
| Workflow Orchestration | Tauruseer + Communication Tools | $0.00 | Tauruseer helps foster tighter collaboration between SecOps, DevOps, Engineering, & GRC with security workflow orchestration into the tools you already use like JIRA, Azure DevOps, Slack, ServiceNow, and more to speed response and track issues. |
Monitoring | Total Extra Cost $10,000.00*
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Cloud Security Posture Management (CSPM) | Wiz, Orca, Lacework | Starting at $10,000.00 | By integrating CSPM capabilities (API Security, Workload Protection, Serverless Security, Container Security, Infrastructure-as-Code Scanning, and Entitlement Management) approaches to CI/CD pipelines and overlaying Tauruseer's cognitive security analytics XDR, teams can protect their apps and data from external attacks and regulatory challenges. |
| Threat Correlation | Tauruseer + Threat Intelligence | $0.00 | Tauruseer uses cognitive security analytics to correlate, deduplicate, prioritize, and notify based on discoveries, alerts, and observations from various threat intelligence sources, like SIEMs and more. |
Extra Monitoring Capabilities | Total Extra Cost $0.00
| Control | Solution | Extra Cost | Description |
|---|---|---|---|
| Risk Scenarios | Tauruseer | $0.00 | Tauruseer automatically detects risk scenarios in cloud-native application security that include the accidental exposure of critical information, IP, or resources, as well as the illegal access of malicious actors, examples include: inadequate access control, segmentation, and cloud security, as well as a code repository that has been accidentally made public. |
| Risk Combinations | Tauruseer | $0.00 | When numerous risk scenarios are present in tandem or correlated over time, it poses a risk combination. For example, supply chain compromise: in September 2022, detection of a team's code repository changed from private to public, and in January 2023, detection of code tampering in the build process, both events correlated by Tauruseer. |
| Threat Predictions | Tauruseer | $0.00 | The CNAPP is made complete with Tauruseer's ML-driven analytics and adding threat intel to enhance security actions by correlating patterns with ASPM and CSPM risks in real time. This technique highlights which high-risk assets are likely to be compromised and direct attention there, especially with an active attacker present and can easily switch targets. |
CONCLUSION
In today's fast-paced and increasingly digitized world, security and compliance are more critical than ever. Achieving SOC 2 compliance is no longer just a checkbox exercise but a must-have for organizations that want to stay competitive and protect sensitive systems and data. However, overspending on SOC 2 compliance without addressing the root cause of security issues is not a sustainable strategy.
At Tauruseer, we believe in doing real security by integrating security into the development and operations processes to enable SecOps, CloudOps, DevOps, Engineering, and GRC. Our Tauruseer SPACE™ Platform combines GRC(P) concepts with Security Posture Management, providing a unified approach to managing security risks. By embedding security controls, organizations can achieve their SOC 2 compliance requirements while also proactively preventing and responding to security risks.
Our platform provides a comprehensive and integrated solution, including application security posture management (ASPM), software supply chain security (SSCS), and integrated cloud security posture management (CSPM) capabilities. With these capabilities, organizations can achieve their security and compliance objectives, proactively manage their security vulnerabilities, and gain a competitive edge in today's market.
In conclusion, achieving SOC 2 compliance is no longer just about meeting regulatory requirements but a strategic imperative for organizations that want to stay ahead. At Tauruseer, we're committed to helping organizations achieve their security and compliance goals while also proactively managing their security risks.
More news and blogs