Innovation Insight: What Is A Cloud-Native Application Protection Platform (CNAPP) Really?
“Cloud security posture (CSPM) incumbents launched traditional approaches leaving huge gaps, as they don’t understand the needs of modern DevOps pipelines or developers.

Gartner released a report in 2021, "Innovation Insight for Cloud-Native Application Protection Platforms" in which all the CSPM vendors rebranded to, and glazed over what Gartner said. We'll address it here because it is important to clear the industry confusion.
Cloud Security Posture Management (CSPM) platforms won the last huge funding rounds. Wiz, Orca, and Wazuh are very good at what they do, which is to secure infrastructure and the cloud. But what they don't see and keep safe is the code and application layer. Additionally, without automated data science and analytics capabilities using machine learning (ML) algorithms, it is impossible for humans to find potential security threats when they have to rely on manual analysis.
Where's The Gap
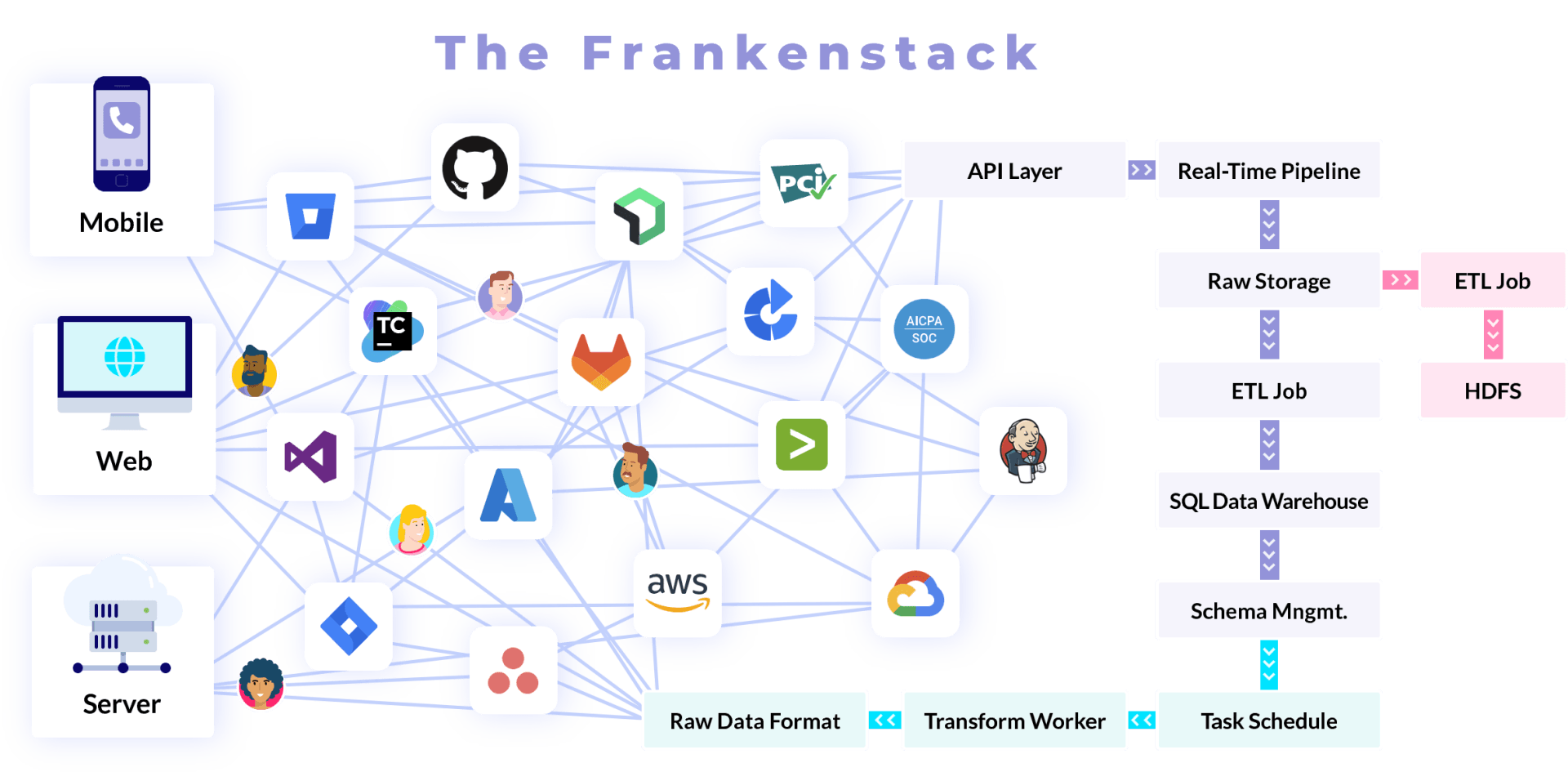
All the mature CSPM vendors repositioned their marketing around CNAPP and it has confused the market. The gap is that cloud-native apps are built using CI/CD pipelines, which are made up of many code repositories for one app, several developers, frameworks, languages, third-party components and dependencies, APIs, and services, etc., which could add up to 40+ tools in each product team. These pipelines are highly automated, and a portfolio of applications can have hundreds or thousands of third-party tools and several active CI/CD pipelines. This means that the growing number of organizations that use modern CI/CD development methods are vulnerable to several tools and applications that could be weak, as well as threats from insiders who have access to source code. Yet, it is very hard for security teams to see what they have, how they are set up, and whether or not they are secure.
There's More To The Frankenstack Than Just Cloud Security Posture
Uncontrolled and insecure DevSecOps has taken a tool-based approach to fix security, leaving teams swimming in complexity and drowning in static reporting and scan data. CSPM platforms shifted left from the firewall...a tiny bit. They sit at the Run & Operate phases.
But the industry is talking Shift Left, again, something CSPM to CNAPP branders just glazed over. What about all the other phases in the SDLC DevOps process: Design, Code, Build, & Deploy? CSPMs aren't focused on these challenges. What is missing is continuous and automated analytics providing contextual risk insights into: code, build process hardening, developer activity and behavior, access, delivery risks, and other application and HUMAN related risks. This is a holistic approach to shifting completely left, then back right, and providing continuous monitoring over the entire stack. "Shift Everywhere". Duh, right?
Gartner Even Called Out The Risks (Which Are Being Ignored By So-Called CNAPPs):
- Enterprise IT departments and development teams simply do not have the necessary expertise. An internal lack of security knowledge was rated as the biggest obstacle to securing cloud-native applications in a DevSecOps pipeline in a recent survey by Gartner.
- Adoption may be stymied by an organization's lack of maturity in regards to the development of cloud-native applications.
- Existing enterprise security protection vendors (e.g., CWPP, WAF, and WAAP vendors) aren't always great at integrating into development, and they often don't understand the requirements of today's DevOps-style development pipelines or developers.
- Security tooling that generates false positives or low-risk findings wastes the developer's time and is therefore unacceptable.
- Open Source Software (OSS) tools may have been adopted by developers to accomplish some of the goals of CNAPP, but not all, leaving the security team with blind spots in terms of visibility and control.
- There may be blind spots in visibility and control if cloud-native application security strategies don't cover all forms of development artifacts (see Building Sustainable Ecosystems for Cloud-Native Software, The Cloud Native Computing Foundation (CNCF).
- In some companies, the group responsible for managing runtime protection of workloads isn't involved in the selection of application security testing tools, which can lead to siloed purchases. Recent research by Gartner found that unclear boundaries between applications and infrastructure ranked as the third greatest obstacle to successfully securing cloud-native applications. Cloud-native app creators are largely responsible for the growing similarity between these two (see Figure 2 below).
What A Comprehensive CNAPP Platform Looks Like (HINT: CSPM + ASPM)
A cloud native application protection platform (CNAPP) is a platform that offers a variety of security tools and services to protect cloud-native applications from different threats and vulnerabilities without stopping developers from building and deploying applications in a cloud environment.
- Traditional Cybersecurity Approach + Incomplete Zero Trust = "security gates" with vulnerability scans at end of processes, disrupting workflows, and is rifled with too many point solutions. Many of which still remain shelfware, meaning there are often tools are bought and are sometimes not being used at all or used less than their full capabilities. Essentially a "Trust-No-Verify" approach. That's not Zero Trust. Which in turn, makes the CISO's Zero Trust strategy and implementation.... incomplete.
- Modern Agile Cloud-Native Application Security Approach = "security guardrails" in one platform that consolidates point solutions with automated analytics, vulnerability scans, accountability, and governance down to every product team tied to measurable policies...a process that is rapid and fluid is what developers want (and drives better adoption)!
A modern CNAPP aligned with Agile and DevOps has a set of tools, frameworks, and services that SecOps, DevOps, Engineering and Compliance can use to make cloud-native apps that are scalable, reliable, and able to use the cloud's benefits. A complete CNAPP platform shouldn't just focus on the underlying infrastructure as it relates to production (containers, workloads, OS, etc.). It should also include all the people, processes, and technologies across the entire lifecycle for every application or product. Combining the most important parts of an emerging platform category, Application Security Posture Management (ASPM), with CSPM.
Some of the most important parts of a true, comprehensive cloud-native application platform are:
- Support for modern architectures and frameworks for building applications, like microservices and containers.
- Integration with ASPM Security to facilitate risk insights on cloud-based CI/CD tools and services, like code repositories, build servers, ticketing, SCA, and tools for security monitoring and reporting (SAST, DAST, RASP, IAST, etc.) that show how secure cloud-native applications are and help teams find potential security holes and deal with threats.
- Application Security Posture: OSS/Code Vulnerabilities, Application CVEs, Hardcoded Secrets, Vulnerable APIs, Unencrypted Data Flows, Application Misconfiguration or Code Rot, Data Leakage
- Integration with CSPM Security: cloud infrastructure and services, like storage, networking, and computing, so that cloud-native applications can be deployed and managed.
- Cloud Security Posture: OS Vulnerabilities, IAM/Role/Permission Changes, Infrastructure Misconfiguration, Unauthenticated S3 Buckets, Anomalous Clients/Traffic, Suspicious OS Processes, Cloud API/Service Usage
- Automated deployment and scaling features that make it easy and fast to move applications to the cloud and adapt to changes in demand.
- Automated security controls and policies that can be set up quickly and easily to protect cloud-native applications.
- Monitoring and management tools to help developers and operations teams keep track of how well their applications are running and how healthy they are.
- Threat detection and response capabilities, such as the use of machine learning and other advanced technologies to find and deal with potential threats in real time.
- Security features, such as authentication, authorization, and encryption, to protect apps and data in the cloud.
- Collaboration between SecOps, DevOps, and Engineering using integrated tools to help teams work together and connect their applications to other systems and services.
- Compliance and regulatory support to help organizations meet the requirements of different security standards and regulations.
Deliver Comprehensive Software Supply Chain Security With ASPM + CSPM (CNAPP):

Benefits Combining Tauruseer ASPM + CSPM Data Into A Single, Unified Platform
- Better visibility and oversight: With a unified platform, security teams can get a more complete picture of the organization's security posture and find potential vulnerabilities more easily.
- Increased efficiency and automation: A unified platform can simplify security processes, letting teams automate routine tasks and focus on more complex threats.
- Better coordination and collaboration: A unified platform can make it easier for different security teams to talk to each other and work together, making it easier for them to stop threats and respond to them.
- Less money and work: By putting all of an organization's security technologies and processes on a single platform, organizations can lower their costs and make it easier to manage their security posture.
- Better threat detection and response: A unified platform that combines threat predictions and behavioral analytics can help organizations find potential threats faster and take steps to stop them.
Tauruseer doesn't compete with point solutions or CSPM platforms. Instead, it improves correlation and prioritization by tying cloud security and resources to development and build pipelines and automatically spotting malicious behavior earlier to alert the right teams of applications and products that are currently being actively targeted (see Figure 3 below).

Why Tauruseer CNAPP? Risk Modeling + ML-Driven Analytics In Our Cognition Engine
Tauruseer's patented Cognition Engine and PIRATE™ risk model uses proprietary real-time machine learning (ML) to predict threats. Cognitive security analytics uses algorithms and models that have already been built to look at a lot of data and find risks, security threats, and security holes. The Cognition Engine sends out what we call "Cognitions," which are dynamic risk insights as alerts.
The main reason to use the CERM method is the context. Context sends cognitive security actions to the right people so that they can help organizations take steps to prevent or lessen risks in a more collaborative, effective, and efficient way.
The goal of Tauruseer's CERM is to help an organization speed up the Project-to-Product (P2P) Transformation while also improving the organization's overall security posture.
One of the main benefits of using ML-driven cognitive security analytics is that it can find potential security threats by watching for risk scenarios and risk combinations combined with threat data and making suggestions for how to deal with those threats. The Cognition Engine in Tauruseer can find patterns and trends that humans might not notice right away. The Cognitions provide information that drives a CISO and CTO knowledge base as content for remediation guidance to help the rest of the organization make better security decisions.
Overall, combining historical data with real-time machine learning cognitive security analytics helps people proactively respond to security risks more quickly and effectively, limiting the damage they cause.
More news and blogs